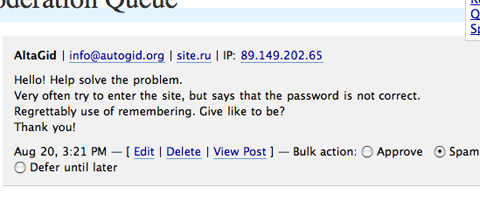
Why sure, anonymous Russian commentor! Here’s my password right here!
Assuming the idea is to harvest valuable passwords from the hopelessly naive, and not something more subtle, it’s an interesting economics problem. Spamming (or in this case, phishing so crude that is looks like spam) works on the assumption that even if only one person in ten thousand ever buys your product, you can make a thousand sales if you send to ten million people. So why not ask a million bloggers for their passwords? Maybe a few will slip up and give you good information.
Whoever wrote the script to send this spam might also consider writing letters to every billionaire on Earth asking for a thousand dollars on the assumption one of them is sure to say yes. After all, there are plenty of billionaires, none of them will miss a thousand dollars, and maybe one will be in an indulgent mood, or senile.
The appeal to such an approach comes from an intuitive or actual appreciation of the fact that [tex]P(\mathtt{totalrejection}) = P(\mathtt{individualrejection})^N[/tex]. That is, if there’s a 90% probability of being rejected on one request, if you ask twice, there’s only an 81% probability that both requests will be rejected. Ask ten times and there’s only a 35% chance all ten will reject. By the time you ask 50 times, and there’s only a 0.5% chance you will get 50 rejections. If the cost of making a request is very low and the benefit of even a single acceptance is high, [tex]P(\mathtt{individualrejection})[/tex] can be very high indeed. This is the probabilistic mechanism which makes spam profitable.
So can that work for spamming a million bloggers to ask for passwords? Or a thousand wealthy people asking for money? Maybe, but it’s different from simple spam advertising. If you’re selling, say, Viagra through an online pharmacy, there’s no cost to you until you also receive the benefit: the customer goes to your automated web site, pays via credit card, and only then do you step in to package and deliver the goods. Here, Anonymous Russian Hacker has to undergo cost without any guarantee of benefit. If I send him a password, he has to visit the site, log in, and look for something worthwhile. And since I know this, it makes trying to lure the hacker into a honeypot much more attractive, making it more likely that that cost will have to be undertaken without increasing the (marginal) probability of benefit.